What is Asset Inventory?
The effectiveness of an ASM initiative is determined by how well the solution records the attack surface and presents the data to the organization. A best-in-class ASM program must include a comprehensive inventory of an organization's growing attack surface. It should also eliminate spreadsheets and manual processes altogether, but it shouldn’t stop there.
The inventory capability of HackerOne Assets allows customers to create and control risk-ranked, custom categories for digital assets across their organization. Over time, it becomes a golden record of global external assets and associated security testing, while accelerating ASM and Vulnerability Management (VM) outcomes.
HackerOne Assets customers can access the inventory capability via a unified UI to manage their attack surface and the security testing scopes. The early users have seen significant improvements in finding unknown internet-facing assets in their attack surface and managing the associated risk. This includes a remarkable +2X improvement in attack surface visibility and control for customers that started their ASM program with HackerOne.
How a Major US Bank Prepared for a Multi-Year Cloud Migration with HackerOne Assets
How it Works
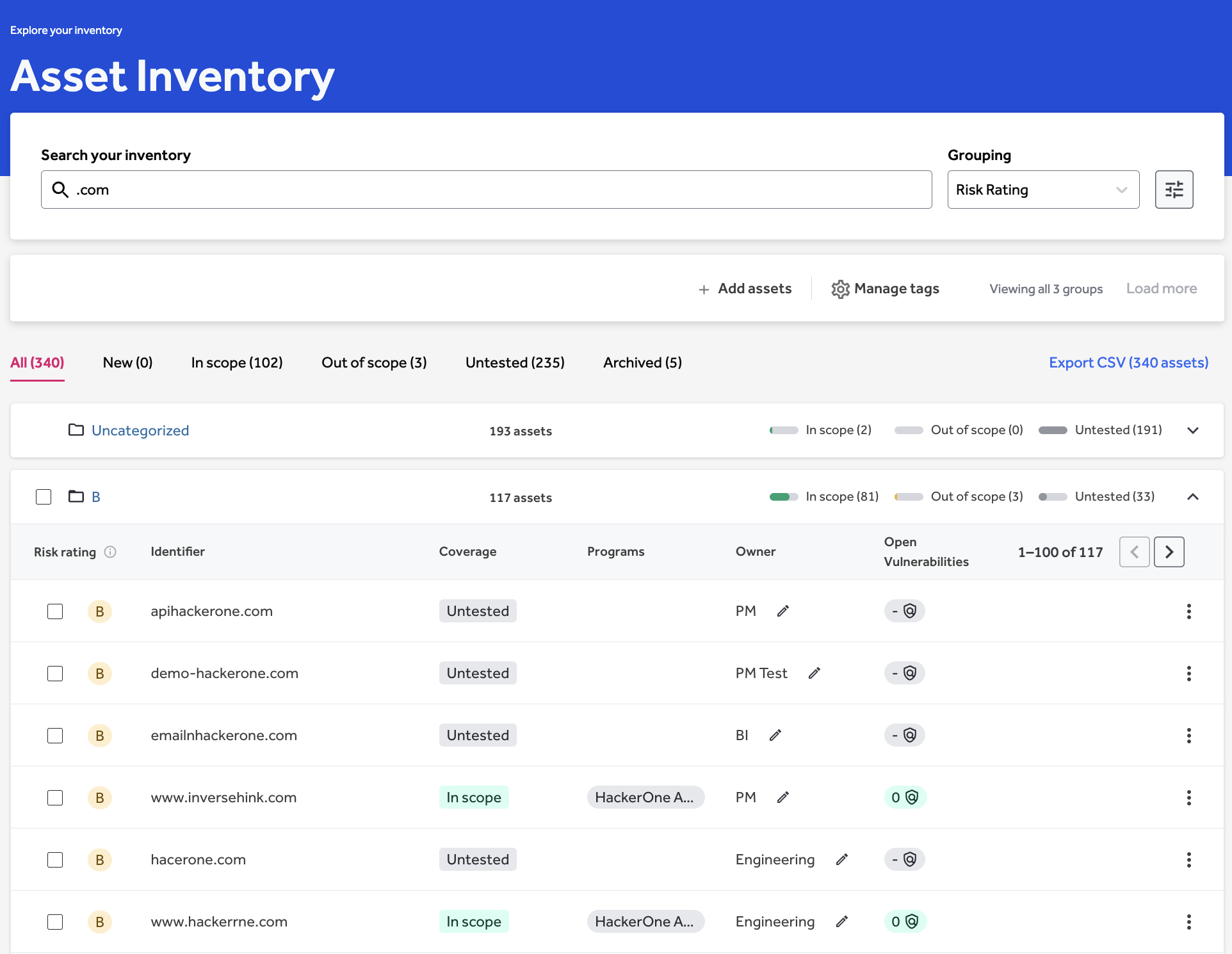
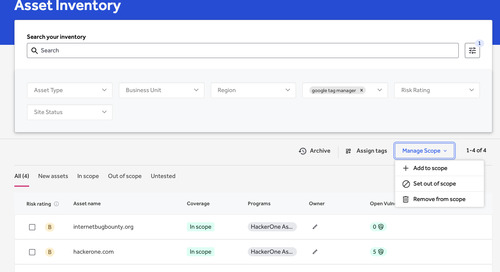
An organization’s inventory shows all new assets and the assets in scope, the coverage of their testing programs, and provides a summary of the open vulnerabilities (Figure 1).
Clicking on a domain group on the inventory page opens a detailed list of all assets under that domain. From there, asset characteristics can be edited individually or in bulk. Each asset listed shows information on testing coverage, program, owner, and open vulnerabilities (Figure 1).
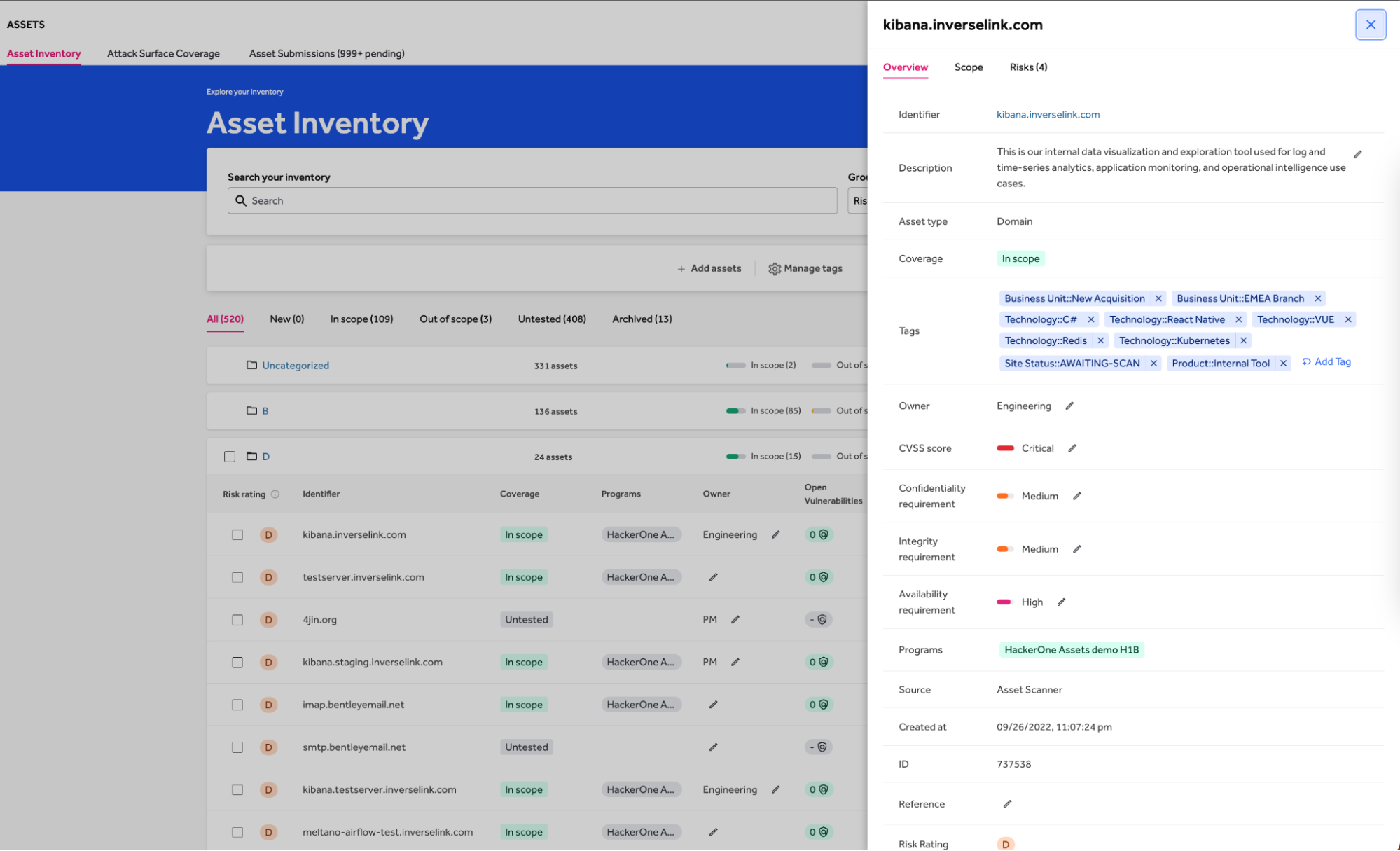
The inventory can scale from hundreds to thousands of assets efficiently and allows custom asset tagging. Assets tagged with technology stack, business unit, or geolocation can be further categorized, filtered, and grouped based on the standard or custom-created tags (Figure 2).
Enriching the Inventory With Relevant Data
Unlike other ASM solutions that only populate the inventory with the results of a single scan, the inventory feature in HackerOne Assets ingests results from multiple sources:
- HackerOne’s continuous attack surface scanner detects risky software by looking at the technology stack and host header..
- Imported data from open-source technologies, other ASM solutions, and homegrown asset management tools in CSV format or through the HackerOne API.
- Assets discovered by HackerOne’s community of security experts to see vulnerabilities from an adversary’s point of view.
Book your free attack surface review, and get an actionable risk snapshot in 60 minutes.
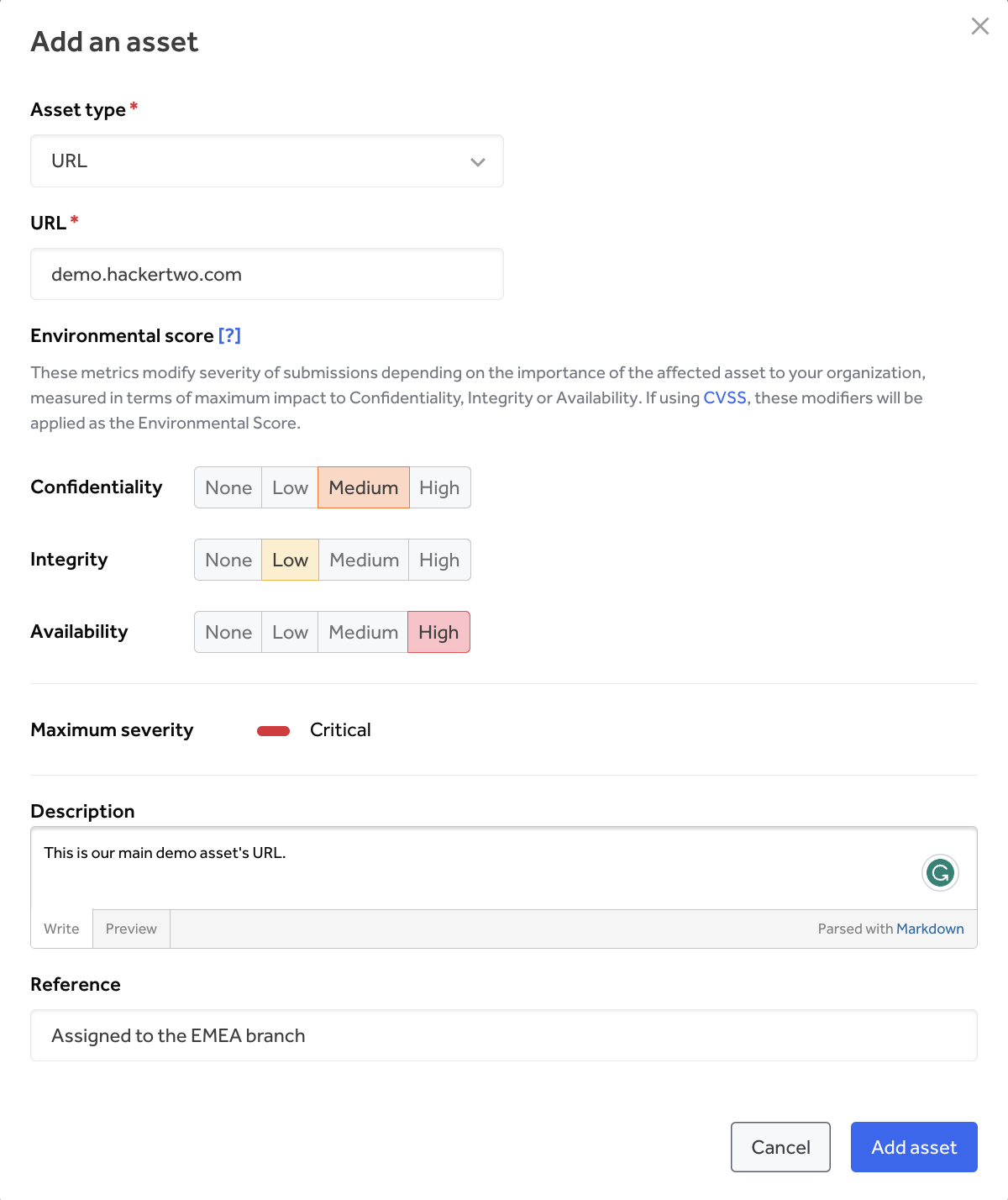
Additional assets can be included from the inventory page by clicking ‘Add an asset’ under the ‘search & filter’ box. A pop-up menu will appear, prompting users to enter asset details (Figure 3).
Exporting Asset Data to CSV
The CSV Export feature allows you to export details related to your assets, including DNS/whois and IP information (Figure 4). It provides all the essential asset metadata in a standard export format, making it easy to share data with your team and improving security efficacy across your organization.
The CSV Export is context-aware and respects the filters and search queries you have applied to the inventory. This ensures that you only export the relevant data you need, saving time and streamlining your asset management process.
Starting Security Testing and Managing Scope From Asset Inventory
While ASM and security testing should go hand-in-hand, they are typically disconnected in the real world. Security teams need a more efficient way to feed newly discovered assets into existing security testing workflows. This creates redundancy in scope management across each pentest, bounty program, and provider their organization works with. To reduce threat exposure, inventoried digital assets must also be risk ranked and remediated fast.
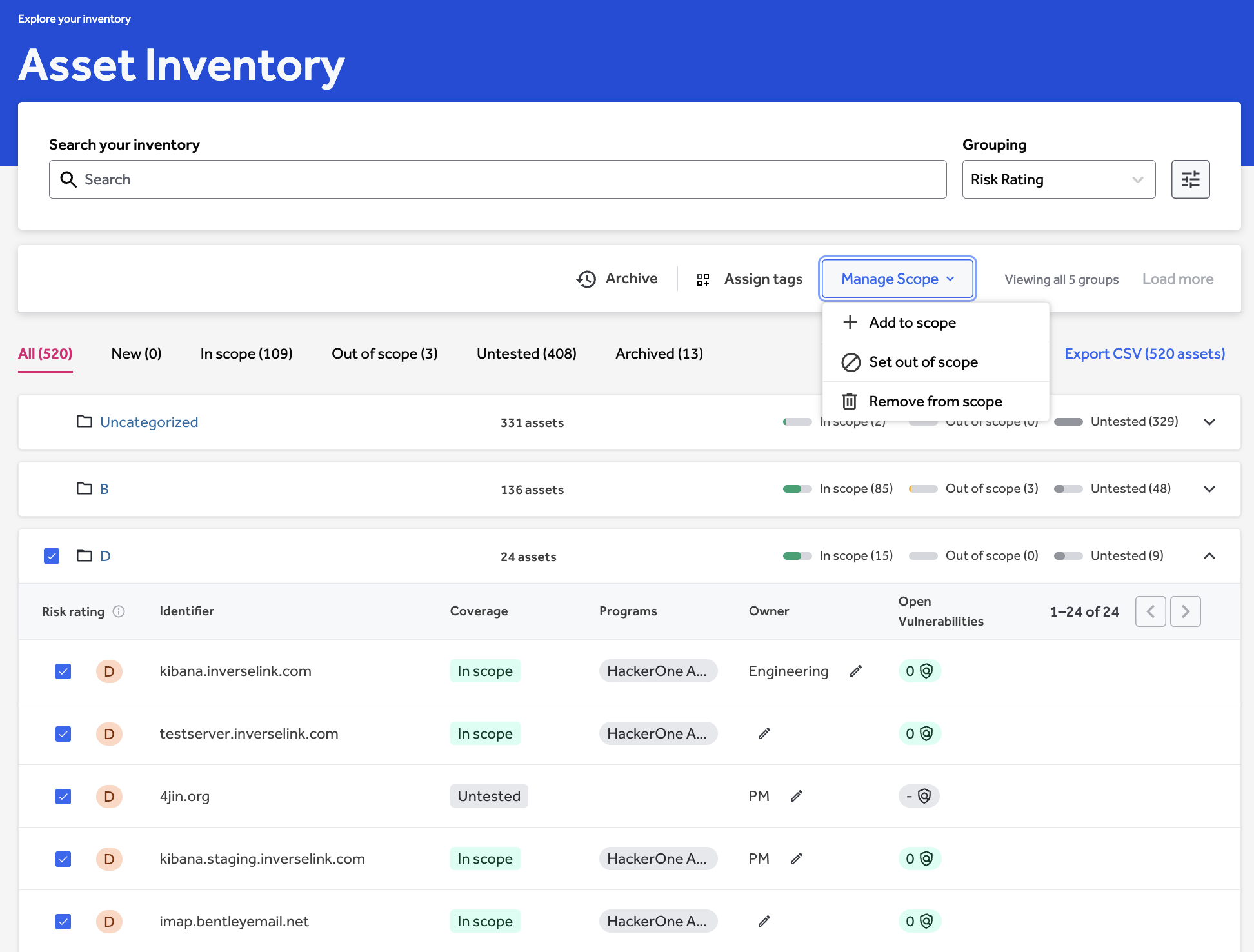
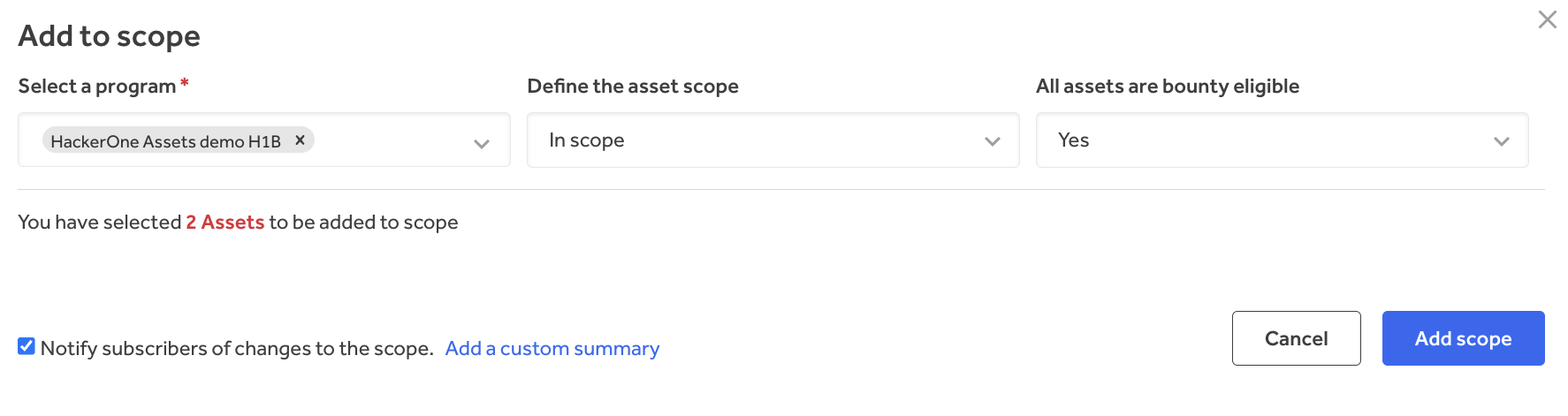
HackerOne addresses this by making it easy for organizations to add newly discovered assets directly to existing adversarial testing scopes within their inventory (Figure 5). A security team can complete basic remediations on a newly discovered asset, then add it to an active bug bounty, VDP, or pentest program (Figure 6). This process ensures that newly identified risks are fed into established risk reduction processes instead of slipping through the cracks.
Read more about Unified HackerOne Scope Management with Burp Suite Support
Scope management supports the selection of one or multiple assets, adding them to active security tests, and modifying the scope and bounty eligibility via drop-down lists. With enhanced control over the scope, security teams can work more efficiently by avoiding the duplication of assets when overseeing multiple tests.
Curious to learn more? Contact us to increase your team’s ability to protect your attack surface and act on what matters most!